This topic contains information about the best practices to follow for using Transparent
Identification in IWSVA.
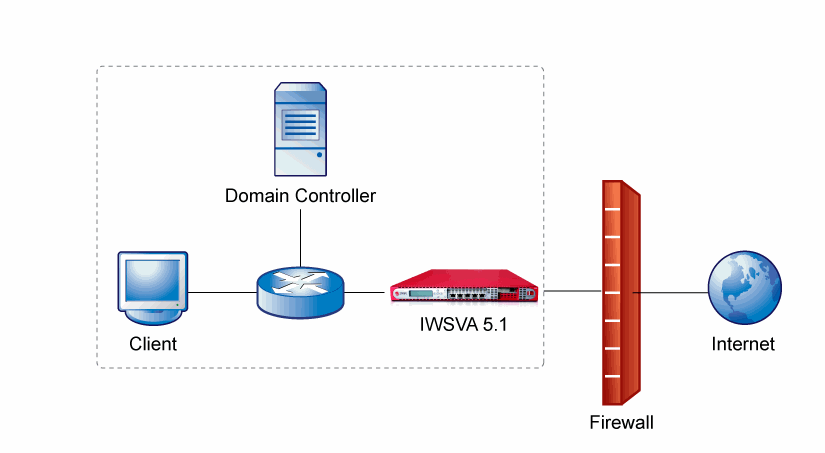
Topology
The figure below shows the typical transparent bridge mode network topology used when
deploying IWSVA in your organization.
In the image, IWSVA sits behind the firewall with access to the Domain Controllers
and client machines required for Transparent Identification. If there is a NAT or
firewall between client machines or Domain Controllers and IWSVA, the Transparent
Identification query might fail.
In your organization, if the domain structure is not a single domain, but a tree or
a forest, Trend Micro recommends that you enable the Global Catalog in the Domain
Controller used by IWSVA as shown in the image. It not only reduces the logon traffic
passing through the Internet and saves your bandwidth, but it also speeds up the log
on process and helps IWSVA to obtain user/group information more quickly.
Settings
Before starting the next procedure, check the following:
-
Domain Controller Settings: Create a new account or use an existing one that belongs to 'Domain Admins' group
in your Domain Controller for IWSVA used to query for user/group information.
-
Client Settings: Configure the 'Windows Management Instrumentation (WMI)' to start automatically and
verify it is started on the clients.
-
Firewall Settings: Verify the Windows firewall or other personal firewall in the client or the Domain
Controller allows WMI traffic to pass.
If you use Windows firewall in your client machines, you can deploy a group policy
to change the default firewall settings in each client machine joined to the domain.
This will automate the client configuration procedure and simplify deployment. See
the following procedures for more information:
Step One: Creating the Group Policy Object and Linking It to the Proper Organizational
Unit
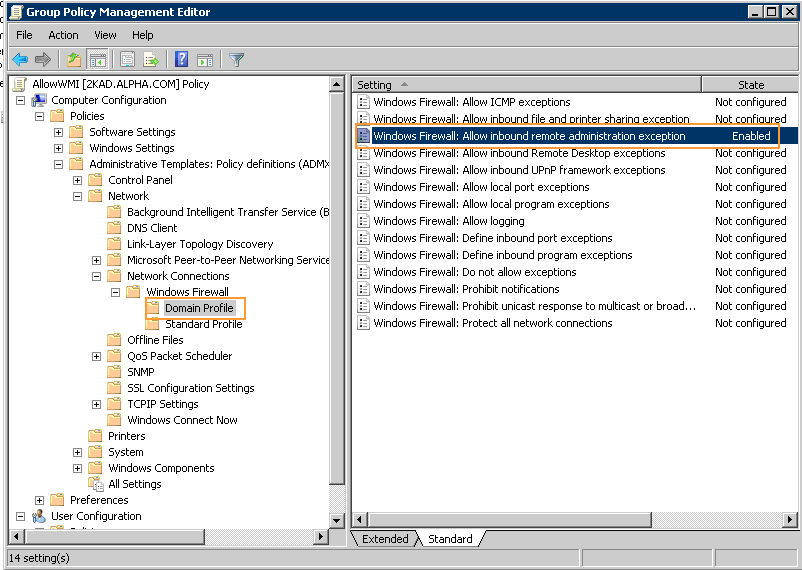
To create a group policy object:
-
Go to the Group Management Policy editor.
-
Go to Computer Configuration > Policies > Administrative Templates > Network > Network Connections
>Windows Firewall.
-
Double-click Domain Profile.
-
Click Windows Firewall: Allow remote administration exception.
-
On the Action menu, select Properties.
-
Click Enable, and then click OK.
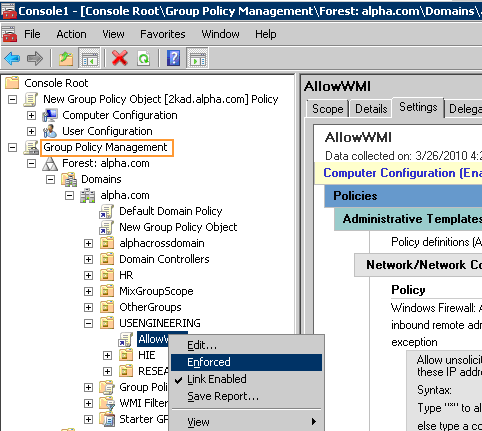
Applying the Group Policy Object to all client machines
To apply the new Group Policy Object to all client machines:
-
Go to the Group Policy Management MMC snap-in. (See image above.)
-
Right-click the newly added Group Policy Object.
-
Select Enforced.
Configuring Transparent Identification
Before starting this procedure, IWSVA should be configured with a valid DNS server
that has good performance for resolving DNS requests. Make sure IWSVA can resolve
the Domain Controller's hostname in the DNS server.
To configure Transparent Identification in IWSVA:
-
Select the Administration > IWSVA Configuration > User Identification | User Identification tab from the main menu.
-
Under the User Identification Method section, check User/group name authorization.
-
Under the User/group Authentication Settings section in the LDAP Settings section,
click the Select LDAP vendor link.
-
In the secondary browser window, select Microsoft Active Directory from the list of supported the LDAP vendors.
-
In the Configure LDAP Connection secondary window, click Save to confirm your LDAP vendor choice.
-
On the User Identification configuration screen, in the LDAP Settings section, type
the LDAP server host name using the Fully Qualified Domain Name (FQDN).
 |
Note
Entering the LDAP server hostname's IP address is also acceptable, but FQDN format
is recommended due to an incompatibility between Kerberos servers and identifying
LDAP servers using their IP address.
|
-
Type the Listening port number used by the LDAP server that you have chosen (Default = 389).
 |
Note
If you have enabled the Global Catalog (GC) port as recommended, change the listening
port to 3268.
|
-
Type the Admin account and password of the new created or existing account of "Domain Admins" group.
You should use the UserPrincipalName for the admin account in the following format:
NT_logon_ID@domain. For example: chris@trendmicro.com
-
Type the Base distinguished name to specify which level of the directory tree IWSVA should begin LDAP searches.
The base Domain Name is derived from the company's DNS domain components; for example,
LDAP server us.example.com would be entered as DC=example, DC=com.
-
Select the LDAP authentication method to use Advanced (Kerberos Authentication).
-
Additionally, configure the following parameters to use Advanced authentication: (By
default, the following setting will be automatically filled in, when enter 'Tab' button)
-
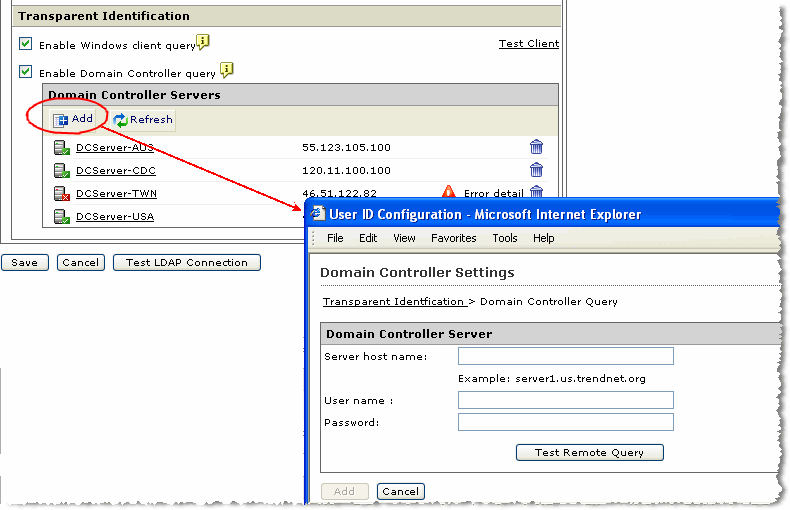
Click the check boxes for Enable Windows client query and Enable Domain Controller query to enable both.
-
Click the Test Client link to test the client connection. It should be successful.
Clicking the check box for Enable Domain Controller query allows IWSVA to receive
the event logs for the Domain Controllers listed and to parse the event logs for user
information.
When the "Enable Domain Controller query" is first enabled, users receive a prompt
to add the Domain Controller server(s) or to refresh the list of Domain Controller
servers. Do the following:
-
Click Refresh to auto-detect Domain Controller servers.
-
If new Domain Controller servers are not auto-detected, add them manually by clicking
Add. The Domain Controller should also list the IPv6 Domain Controller with similar behavior
to that of IPv4 and you can add a dedicated IPv6 Domain Controller here.
-
Type the Domain Controller information in the secondary window, and click Test Remote Query to verify the Domain Controller server connection. (See Figure E-5.)
-
All Domain Controller servers added to the configuration file allow IWSVA to query
the event logs for username and IP address information.
-
Make sure the status of all Domain Controllers in the list is OK as indicated by the
small green check mark before going to next step.
-
If necessary, add information for the additional LDAP servers.
 |
Note
All Active Directory domain controllers used to authenticate users to the domain should
be added to the LDAP server list.
|
-
To verify the information has been entered correctly and IWSVA can communicate with
the LDAP servers that you configured, click Test LDAP Connection on the User Identification page.
A message box appears, indicating that you have successfully contacted the LDAP server.
-
Click Save.